Email Spoofing
There is very little you can do to stop a Spoofed email from coming your way, and because of this we have all experienced it: the email that seems to come from a colleague, or an old friend from high school. Although, something about this email address does not look quite right. Didn’t this fiend have a Yahoo email and not a Hotmail account? Likewise, the body of the email says something like “Hey, I thought you would be interested in this…” followed by an unfamiliar website link. That link will lead to a destination which might wish to sell you something. Or… infect you with a virus. Or any number of bad things that you don’t want.
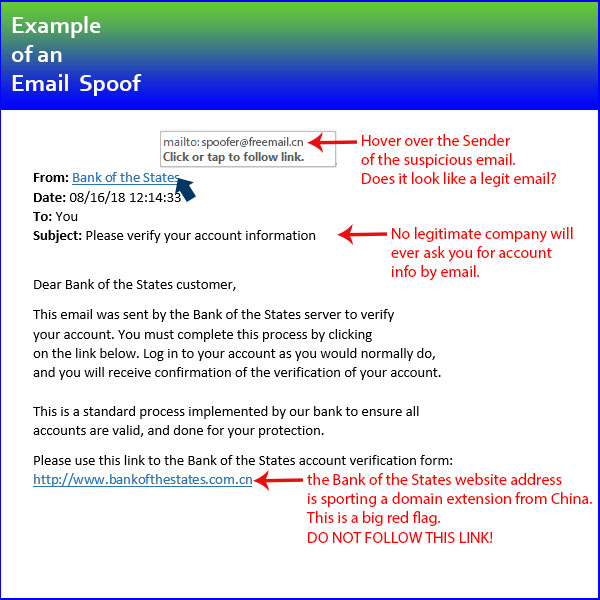 There is a myriad of creative ways how a Spoofer would have been able to acquire your name and email address, so suffice it to say that you should always be very careful to guard your personal information. However the Spoofer did it, the Spoofer mined your name and email address, and has (at least) the name of a friend of yours. Let’s call your friend Bob. Then the Spoofer went to a free email service (like Hotmail or Gmail) and created an email account with Bob’s name on it. Now the Spoofer emails you, using the new email the Spoofer created under Bob’s name, and poses as your friend Bob. Now that the Spoofer is in contact with you, the is hope to profit off of you by getting you to sharepersonal or financial information.
There is a myriad of creative ways how a Spoofer would have been able to acquire your name and email address, so suffice it to say that you should always be very careful to guard your personal information. However the Spoofer did it, the Spoofer mined your name and email address, and has (at least) the name of a friend of yours. Let’s call your friend Bob. Then the Spoofer went to a free email service (like Hotmail or Gmail) and created an email account with Bob’s name on it. Now the Spoofer emails you, using the new email the Spoofer created under Bob’s name, and poses as your friend Bob. Now that the Spoofer is in contact with you, the is hope to profit off of you by getting you to sharepersonal or financial information.There are some things you can do about this, and some things you cannot do about this. First, let’s begin with the things you can’t.
What you Cannot Do:
Because there are no core protocols, and therefore no mechanisms for authentication, in the creation of free emails, you cannot stop a Spoofer from setting up fake email accounts and emailing you if the Spoofer gets his hands on your email. So, honestly, the prevention is far more effective than any cure: Avoid any action that might make your email address available to people you don’t know. Your ability to prevent the reception of emails is limited to whatever filters your email system might have in place. Email filters, however, work best on filtering out mass emails attempting to sell car insurance to you; they do not work so well on emails from Bob.



Great information! I get these emails occasionally and this info is really helpful. I’ll definetly be making sure that this article makes it’s way to all of my clients!
Thank you, Cassandra! To be sure, to be forewarned about how to detect spoofers is to be forearmed. Thank you for your great feedback!